
Ascendo Pte Ltd
- Address: 85, Playfair Road #06-02 Tong Yuan Industrial Building Singapore 368000
- Tel: +65 6741 1218
- Email: [email protected]
© 2025 Ascendo Pte Ltd. All Rights Reserved. Website By Creative eWorld Pte Ltd.

The VAULT Visitor Management Systems software enables a comprehensive operation, with numerous functions such as check-in and checkout, location, name tag printing, report preparation, asset and package management, service provider registration, and much more.
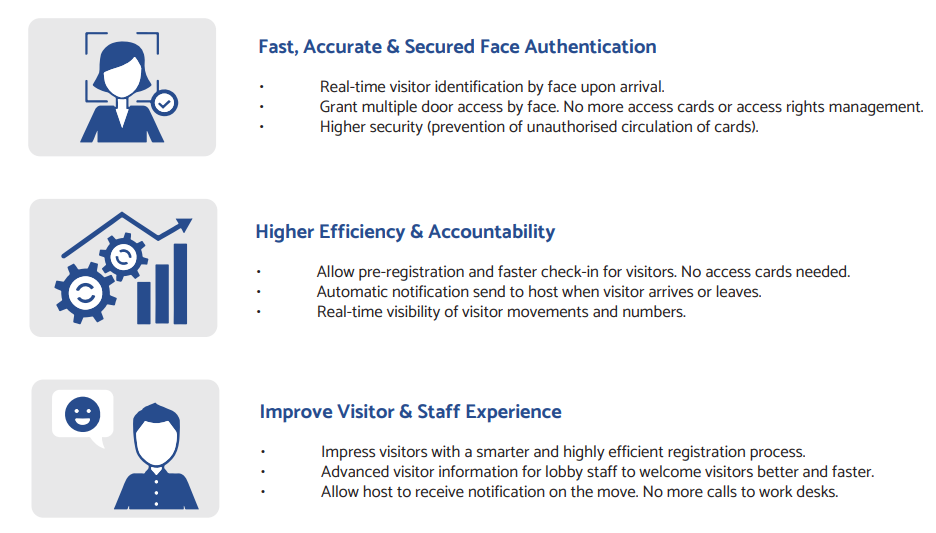
Is an Enterprise level visitor management registration system, with the latest resources, in accordance with the needs of companies that require maximum agility on temporary credential control.

 Automatic CheckOut
Automatic CheckOutWhen working in conjunction with the VAULT Site Systems, this solution offers the resource of automatic cancellation of the registered credential number when the credential is read by the safe card-collector reader, optimizing the operation and drastically increasing security

OCR helps to fill up visitor’s name and ID no. By taking a photo of the visitor’s ID. This helps to speed up the registration process as well as making sure that visitor information is captured accurately without human error.
A tool to create the layout of labels and to print credentials which enables the creation of a professional design
Combination of Vault Cloud VMS with Falco Face Reader is truly designed an automation process visitor pre-registration supporting facial recognition and enabling access upon the host’s validation.
Equipped with dashboard for status monitoring and comprehensive reporting. It’s convenient and integrates seamlessly, supporting unlimited host and/or visitor registrations as well as multi-tenant applications.

Designed with GDPR Compliance and is largely based on its ability to recognize facial features.
Every individual has their own unique set of distinguishable facial features, known as nodal points.
These nodal points are impossible to replicate and can be set for automatic erosion after a set time has elapsed. No actual photo images are stored on client networks, meaning visitor identities remain secure and safe.
© 2025 Ascendo Pte Ltd. All Rights Reserved. Website By Creative eWorld Pte Ltd.

© 2025 Ascendo Pte Ltd. All Rights Reserved. Website By Creative eWorld Pte Ltd.